Thursday, December 13, 2012
FREE TODAY ONLY: Kindle Edition of The How-To Geek Guide to Windows 8
Amazon is offering the Kindle Edition of the How-To Geek Guide to Windows 8 (nearly 1000 pages!!) for free today only! I use the How-To-Geek website all the time and now is your chance to get what should be an amazing book on Windows 8.
Wednesday, December 05, 2012
ATT iPhone users in Central PA may see "DAN" as their carrier
Some ATT iPhone 3/4/4s users in Central PA are seeing their carrier change to "Dan" instead of ATT. ATT is aware of the glitch and are working to fix it. More details can be found in this Pennlive.com article.
Tuesday, December 04, 2012
You can now search the Windows Store for your Win 8 Apps
While I'm not a fan of Microsoft's new Windows 8 OS on laptops/desktops (for business or personal use), this new website could make it easier for those of you that do to find the "Metro" style apps that you are itching to install.
Apple and Google both have web based versions of their app stores for searching, browsing and sharing. Microsoft's Windows Store for Windows 8 (Surface, Surface RT, Windows 8 & Windows 8 Pro) is only available inside Windows 8 itself.
With MetroStore Scanner you can now search for apps for your Windows 8 based computer much easier.
via ghacks
Apple and Google both have web based versions of their app stores for searching, browsing and sharing. Microsoft's Windows Store for Windows 8 (Surface, Surface RT, Windows 8 & Windows 8 Pro) is only available inside Windows 8 itself.
With MetroStore Scanner you can now search for apps for your Windows 8 based computer much easier.
via ghacks
Monday, June 11, 2012
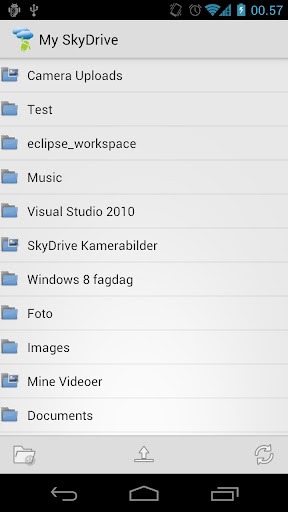
Android App: SkyDrive Explorer - Direct access to your SkyDrive files
With Microsoft's push toward Windows 8 - they are making SkyDrive an integral part of the OS to make sharing easier. Now you can have direct access to your files on your Android device with SkyDrive Explorer app.
You can find more details at the source link below and pick up the app at the Google Play store.
Source: Redmond Pie
You can find more details at the source link below and pick up the app at the Google Play store.
Source: Redmond Pie
Wednesday, June 06, 2012
IMPORTANT!! Two LinkedIn Security issues
If you haven't seen the LinkedIn related headlines over the past 36 hours take heed: Change your password now and if you are using the mobile app on Android or iOS update your app. There have been reported password leaks from the LinkedIn servers as well as the mobile apps scraping your personal calendar information from your mobile device.
You can find more details in the articles below:
Computerworld - Password leak
CNET - Mobile App Privacy Issues
LinkedIn Blog - Password leak
LinkedIn Blog - Mobile App Privacy Issues
You can find more details in the articles below:
Computerworld - Password leak
CNET - Mobile App Privacy Issues
LinkedIn Blog - Password leak
LinkedIn Blog - Mobile App Privacy Issues
Mobile Device Management vendor comparison
I've already posted about Mobile Device Management software, but Enterprise IOS provides a great vendor & feature comparison chart from real world users.
This could be an invaluable resource to anyone trying to manage all the BYOD issues that arise these days.
Check out the MDM Vendor & Feature comparison chart here.
This could be an invaluable resource to anyone trying to manage all the BYOD issues that arise these days.
Check out the MDM Vendor & Feature comparison chart here.
Monday, June 04, 2012
Windows 8 32bit can still run 16bit apps
I know there are more than a few companies out there that are still needing to run legacy software 10 or more years old that are sticking to old versions of Windows just to make sure they software still works. There is always the option of running an old OS in a VM, but there are huge security risks in doing so especially if the system needs to be connected to an IP network. Most of these legacy applications rely on 16bit computing and the past half decade, Microsoft has been moving from 32bit computing to 64bit computing. Many industry market share surveys show that the 64bit versions of Windows 7 dominate the marketplace. This is why it had been rumored that Microsoft was not going to create a 32bit version of Windows 8, but they most definitely are making 32bit Windows 8. What was unclear was if 16bit computing could still occur inside the Windows 8 32bit. Microsoft's Building Windows 8 Twitter account has a post that does clear this up. 16bit applications can run on the 32bit version just not the 64bit version (and the same remains true for Windows 7)
This is just another reason to update to Windows 7 or Windows 8 when it is released. Just be sure you are utilizing the correct version (32bit or 64bit) for your purposes.
This is just another reason to update to Windows 7 or Windows 8 when it is released. Just be sure you are utilizing the correct version (32bit or 64bit) for your purposes.
Thursday, May 31, 2012
Emergency radios that power your gadgets too!
Eaton is updating its self-powered hand-cranked emergency radios with USB ports to charge your portable devices.
This would have been really nice last September during the dark times of the Susquehanna River flood in when power was shut off. I would have been able to stay up-to-date on the river levels and any other necessary news as well as charge my iPhone. There are multiple models to suit your needs and price ranges. For more information check out the Engadget article linked below.
Source: Engadget
If you just need to charge those gadgets without the radio, Sony is coming out with a new hand-cranked USB charger (and it even has an AC powered battery too!). This would be a great addition to my camping gear.
CNET's article provides details on this potentially $100 device, as well as comprehensive link on emergency cell phone charging options.
This would have been really nice last September during the dark times of the Susquehanna River flood in when power was shut off. I would have been able to stay up-to-date on the river levels and any other necessary news as well as charge my iPhone. There are multiple models to suit your needs and price ranges. For more information check out the Engadget article linked below.
Source: Engadget
If you just need to charge those gadgets without the radio, Sony is coming out with a new hand-cranked USB charger (and it even has an AC powered battery too!). This would be a great addition to my camping gear.
CNET's article provides details on this potentially $100 device, as well as comprehensive link on emergency cell phone charging options.
Tuesday, May 29, 2012
Humor: How to use a dual screen setup
The image speaks for itself:
While it is humorous to those of us that constantly use dual screens at home and at work, it also shows that some user education/training is necessary. Every time I upgraded a user to a dual screen setup, I spent more than just a minute or two explaining, many times it was a 15-30min training session going over their specific job tasks and how to manage them differently with dual screens.
And to leave you with a tip, this article from ComputerWorld offers 6 ways to use multiple displays with your laptop with a few of them being quite creative.
While it is humorous to those of us that constantly use dual screens at home and at work, it also shows that some user education/training is necessary. Every time I upgraded a user to a dual screen setup, I spent more than just a minute or two explaining, many times it was a 15-30min training session going over their specific job tasks and how to manage them differently with dual screens.
And to leave you with a tip, this article from ComputerWorld offers 6 ways to use multiple displays with your laptop with a few of them being quite creative.
Friday, May 25, 2012
Stuff your Kindle full of RSS content
Just a quick post here. Would you like to get some of your favorite website content on your Kindle for easy "offline" reading? Check out kindlefeeder.com for both free and paid accounts to push all that web content down to your Kindle
Thursday, May 24, 2012
Friday is Geek Pride Day - how are you going to show it?
Yes. I am a geek. I have been going all the way back to my high school years. What better way to celebrate it than Geek Pride Day (see why at Wikipedia) on Friday, May 25, 2012. This day has also become a sort of "Geek Appreciation" day as well for all of those out there that rely on us geeks in some form or fashion. So make sure that geek in your life knows you appreciate him or her.
While I will be on a camping trip on Friday, I will be celebrating by wearing this shirt:
Here's a few more of my geek shirts:
While I will be on a camping trip on Friday, I will be celebrating by wearing this shirt:
Here's a few more of my geek shirts:
Happy Geek Pride Day!
Monday, May 21, 2012
Tools now available to pull all your data from Apple's iCloud
This article from InformationWeek outlines a new digital forensic tool that can be used to pull down all your data from Apple's iCloud - including all your iPhone & iPad data if you backup to iCloud like Apple would like you to. While this tool from Moscow-based ElcomSoft, is most likely to be used by some type of law enforcement entity, that does not mean it could not be used in a harmful manner. And the tool does require a valid iTunes/iCloud account username & password to gain access, which means the tool is not "hacking" it's way in to a users files. That sounds nice, but over the past few years there have been a large number of iTunes accounts targeted for attack by hackers & identity thieves - most recently documented in this ZDNet article "Anatomy of an iTunes Store Account Hack". Since most users are using the same credentials for their iCloud account as their iTunes account, it would not be much of a stretch to see these same hackers to begin going after both the iTunes and iCloud accounts for their valuable data.
iCloud accounts can store your music, track your device (and you if you're carrying it), and have email setup on it, but it can also be used to backup your iPhone or iPad. Prior to iOS 5, users had to utilize iTunes to activate, backup and restore their devices and were provided with an option to encrypt these backups. These encrypted backups would make it nearly impossible for anyone that gained physical access to your computer. With iOS 5 users can now go "PC free" and perform their backup and restores via iCloud, but these backups apparently are not encrypted on Apple's servers.
Why should you be concerned about where your backups are stored and who has access to them?
ElcomSoft marketing director Olga Koksharova explains in his blog post: "iCloud backups hold essentially the same information as stored in offline backups, which includes accounts and passwords , call logs and text messages, calendars, appointments, contacts and organizer information . Pictures and Web browsing history including URLs of recently visited sites are also included." Who would really want all of that information on any remote backup service without being encrypted? Not me.
While there is a setting on your iDevice to change your iCloud backup options, the easiest way to do this is from the iTunes summary screen for your device that shows up when you have it plugged into your computer. This setting is about halfway down the screen and is very easy to locate (see below):
Just make the change to backup locally and then select the option to encrypt your backups and choose your password. Once this is complete, iTunes will backup your device when you Sync it with your computer or you can just right click on your device and select backup. Your iDevice may no longer be "PC Free" but your data will be quite a bit safer.
Source: Information Week
iCloud accounts can store your music, track your device (and you if you're carrying it), and have email setup on it, but it can also be used to backup your iPhone or iPad. Prior to iOS 5, users had to utilize iTunes to activate, backup and restore their devices and were provided with an option to encrypt these backups. These encrypted backups would make it nearly impossible for anyone that gained physical access to your computer. With iOS 5 users can now go "PC free" and perform their backup and restores via iCloud, but these backups apparently are not encrypted on Apple's servers.
Why should you be concerned about where your backups are stored and who has access to them?
ElcomSoft marketing director Olga Koksharova explains in his blog post: "iCloud backups hold essentially the same information as stored in offline backups, which includes accounts and passwords , call logs and text messages, calendars, appointments, contacts and organizer information . Pictures and Web browsing history including URLs of recently visited sites are also included." Who would really want all of that information on any remote backup service without being encrypted? Not me.
While there is a setting on your iDevice to change your iCloud backup options, the easiest way to do this is from the iTunes summary screen for your device that shows up when you have it plugged into your computer. This setting is about halfway down the screen and is very easy to locate (see below):
Just make the change to backup locally and then select the option to encrypt your backups and choose your password. Once this is complete, iTunes will backup your device when you Sync it with your computer or you can just right click on your device and select backup. Your iDevice may no longer be "PC Free" but your data will be quite a bit safer.
Source: Information Week
Friday, May 11, 2012
Microsoft Office & Sharepoint for the iPad
Microsoft may be missing the boat by not developing iPad versions of their enterprise applications. While there have been rumors of Office for the iPad, this has yet to materialize. This is where CloudOn stepped in and began offering a "desktop in the cloud" that provides access to full versions of Word, Excel and PowerPoint via a free app for both the iPad and Android tablets. CloudOn's "office" product integrates with Dropbox, Box & Google's Drive to allow you to create and edit documents and have them sync down to your laptop or desktop.
There are other apps that will allow you to create and edit Microsoft Office documents directly on your tablet that also offer integration with cloud storage services, but none of them offer the full native desktop application experience that CloudOn's service provides. CloudOn also has paid subscriptions to their service to provide more features and functionality.
Things brings us to SharePoint. Viewing SharePoint sites via Safari works, but if you need to interact with them in any way, problems begin to become quite evident. Two companies are working to resolve this issue by bringing iPad apps to the market: SharePlus: SharePoint Mobile Client by SouthLabs and harmon.ie: SharePoint Mobile Client by harmon.ie. Each apps costs $19.99 and will work on both the iPad and the iPhone making the market for these much larger than if they just supported Apple's iconic tablet. And while that's considered a relatively hefty price for a mobile app, this would be considered average for an enterprise level app. The makers of such apps understand that individuals and companies may be reluctant to spend more than a few dollars per app and tend to offer free or low cost "lite" versions of their apps that provide basic functionality. SharePlus Lite: SharePoint Mobile Client and harmon.ie Lite: SharePoint Mobile Client are both free and I highly recommend all of you out there that need SharePoint access on the go, to download both free apps and see which one works best for you. If you are an Office 365 user, the SharePlus apps will more than likely be the best choice.
So you see, the demand is there for native access to Microsoft's Office & SharePoint on the iPad and companies are stepping up to meet this demand. Is Microsoft ignoring the needs of its users? I do not know, but as was seen in the handling of the rumored Microsoft Office on iPad reports earlier this year, Microsoft does seem to be missing the fact that users want access now and could be very reluctant to spend more money on an "official" app if they already have a solution that works.
There are other apps that will allow you to create and edit Microsoft Office documents directly on your tablet that also offer integration with cloud storage services, but none of them offer the full native desktop application experience that CloudOn's service provides. CloudOn also has paid subscriptions to their service to provide more features and functionality.
Things brings us to SharePoint. Viewing SharePoint sites via Safari works, but if you need to interact with them in any way, problems begin to become quite evident. Two companies are working to resolve this issue by bringing iPad apps to the market: SharePlus: SharePoint Mobile Client by SouthLabs and harmon.ie: SharePoint Mobile Client by harmon.ie. Each apps costs $19.99 and will work on both the iPad and the iPhone making the market for these much larger than if they just supported Apple's iconic tablet. And while that's considered a relatively hefty price for a mobile app, this would be considered average for an enterprise level app. The makers of such apps understand that individuals and companies may be reluctant to spend more than a few dollars per app and tend to offer free or low cost "lite" versions of their apps that provide basic functionality. SharePlus Lite: SharePoint Mobile Client and harmon.ie Lite: SharePoint Mobile Client are both free and I highly recommend all of you out there that need SharePoint access on the go, to download both free apps and see which one works best for you. If you are an Office 365 user, the SharePlus apps will more than likely be the best choice.
So you see, the demand is there for native access to Microsoft's Office & SharePoint on the iPad and companies are stepping up to meet this demand. Is Microsoft ignoring the needs of its users? I do not know, but as was seen in the handling of the rumored Microsoft Office on iPad reports earlier this year, Microsoft does seem to be missing the fact that users want access now and could be very reluctant to spend more money on an "official" app if they already have a solution that works.
Monday, April 30, 2012
Friday, April 27, 2012
How Do I Get eBooks & Other Documents to My Kindle?
While the Amazon eBook store is wonderful, you might find deals elsewhere or download free eBooks or just have some other documents you would like to read on your Kindle. If you don't own a Kindle, but have an iPad/iPhone/iPod Touch, you can also use the Kindle app to read them as well.
If this sounds like something you would be interested in, check out all the details at How-To Geek.
If this sounds like something you would be interested in, check out all the details at How-To Geek.
Thursday, April 26, 2012
Looking for an All-in-One Mobile Device Management Solution?
In many businesses these days, it is becoming increasingly common for the every day worker to request access to their email and other company resources on their personal smartphone. In order to secure your company's data if (and when) those phones turn up missing or stolen, you need to have a good mobile device management solution. I know there are a few of these out there....Good Technologies , Odyssey Software and a number of others. Even Microsoft Exchange 2010 SP1 can do a little more than rudimentary management these days.
Well Research in Motion (RIM) jumped into the fray with their BlackBerry Mobile Fusion suite. We all know that BES + BlackBerry smartphones & devices make your date quite secure, but it is highly unlikely these days that all the phones in your company are BlackBerries. While Mobile Fusion does not replace BES for actual BlackBerry devices, it can be used in conjunction. But what's more important is that Mobile Fusion supports Android phones & tablets as well as Apple's iPhones & iPads.
While I've not used this MDM, it does look worth testing out, and the 60 day trial with a few client licenses included is just what any business would want. And what would pricing be after the trial if you would decide to begin using Mobile Fusion? RIM's initial press release information did not specify pricing, but this article from CNET says that Client Access Licenses will start at $99 per user or $4 per user per month and will allow for volume discounts.
Well Research in Motion (RIM) jumped into the fray with their BlackBerry Mobile Fusion suite. We all know that BES + BlackBerry smartphones & devices make your date quite secure, but it is highly unlikely these days that all the phones in your company are BlackBerries. While Mobile Fusion does not replace BES for actual BlackBerry devices, it can be used in conjunction. But what's more important is that Mobile Fusion supports Android phones & tablets as well as Apple's iPhones & iPads.
While I've not used this MDM, it does look worth testing out, and the 60 day trial with a few client licenses included is just what any business would want. And what would pricing be after the trial if you would decide to begin using Mobile Fusion? RIM's initial press release information did not specify pricing, but this article from CNET says that Client Access Licenses will start at $99 per user or $4 per user per month and will allow for volume discounts.
Wednesday, April 25, 2012
Windows Malware - Ransomware: Pay me to boot your computer.
Trend Micro has released some information on a new group of bookit malware that is part of a hybrid attack on users computers. The infection vector could be any an unpatched Windows, Flash, Java, Acrobat or other vulnerability. Once infected, the malware will download multiple different types of malware (such as a Fake Antivirus program) including the ransomware. Once executed, the ransom malware will infect the Master Boot Record (MBR) of the system Hard Drive. While this is not unusual these days (the TDSS/Aleuron family uses this technique), this new malware will display a message on boot (most likely non-English) asking for money to get an encryption key to allow the computer to continue to boot into Windows.
This type of infection (MBR) is highly difficult to resolve remotely, and usually requires "offline" manual cleanup utilizing specialized boot-disks and sometimes even the original Windows install media. Should you run into this type of infection, be aware you are going to have at least 1 day of downtime in order to get the system cleaned.
Bitdefender & F-secure have posted information on a different type of ransomware that encrypts your files then changes the extensions (.doc, .pdf, etc.) to CRYPTED! thereby making it difficult to run programs or open documents. This ransomware right now has been seen targeting users of peer-to-peer file sharing services, but could begin spreading through email via SPAM bots as well.
This type of infection (MBR) is highly difficult to resolve remotely, and usually requires "offline" manual cleanup utilizing specialized boot-disks and sometimes even the original Windows install media. Should you run into this type of infection, be aware you are going to have at least 1 day of downtime in order to get the system cleaned.
Bitdefender & F-secure have posted information on a different type of ransomware that encrypts your files then changes the extensions (.doc, .pdf, etc.) to CRYPTED! thereby making it difficult to run programs or open documents. This ransomware right now has been seen targeting users of peer-to-peer file sharing services, but could begin spreading through email via SPAM bots as well.
Tuesday, April 24, 2012
Android App: CallTrack
Almost daily for the past few years, I've been going through my task list, calendar items, and phone call log to set my schedule for the next few days. This has always been a tedious and time consuming process, so anything to make it easier would be appreciated. The new app called CallTrack could do just that.
CallTrack syncs your phones call activity to your Google Calendar. You can select the type of calls to log (incoming, outgoing, and missed) and the calendar to log them in. You can also dump your current call log to your calendar.
Using this app in conjunction with the Google Calendar Sync for Outlook program, you could have access to your call logs inside Outlook to make it easier to schedule any calls that may need returned the next day. Having this call log in your calendar could also make it easier to remember who you helped through out the day to ensure you are able to account for any billable time to a client.
Check out CallTrack in the Google Play store
Source - Redmond Pie
CallTrack syncs your phones call activity to your Google Calendar. You can select the type of calls to log (incoming, outgoing, and missed) and the calendar to log them in. You can also dump your current call log to your calendar.
Using this app in conjunction with the Google Calendar Sync for Outlook program, you could have access to your call logs inside Outlook to make it easier to schedule any calls that may need returned the next day. Having this call log in your calendar could also make it easier to remember who you helped through out the day to ensure you are able to account for any billable time to a client.
Check out CallTrack in the Google Play store
Source - Redmond Pie
Monday, April 23, 2012
Mac Malware - More Threats
F-secure has a great article that goes over the new threats that have popped up recently and have been overshadowed by all of the Flashback news.
Included in this article is information on more malware exploiting Microsoft Office for Mac vulnerabilities going back to Mac Office 2005 & 2008 in combination with the Java vulnerability used in the Flashback malware. This new malware is called SabPub.
Please make sure you have the latest service packs installed by using the Microsoft Office updater application that was installed as part of the Office Suite itself.
Earlier in April, Microsoft released Service Pack 2 for Mac Office 2011 which takes the version number up to 14.2.0. This service pack not only fixes vulnerabilities, it fixes a large number of issues with Outlook that will result in a generally more stable connection with Exchange. But there have been a number of problems with this update and Microsoft has removed the update until it can resolve the problems and re-issue the update.
Included in this article is information on more malware exploiting Microsoft Office for Mac vulnerabilities going back to Mac Office 2005 & 2008 in combination with the Java vulnerability used in the Flashback malware. This new malware is called SabPub.
Please make sure you have the latest service packs installed by using the Microsoft Office updater application that was installed as part of the Office Suite itself.
Earlier in April, Microsoft released Service Pack 2 for Mac Office 2011 which takes the version number up to 14.2.0. This service pack not only fixes vulnerabilities, it fixes a large number of issues with Outlook that will result in a generally more stable connection with Exchange. But there have been a number of problems with this update and Microsoft has removed the update until it can resolve the problems and re-issue the update.
Thursday, April 19, 2012
Adobe Acrobat Reader marks major security update
Earlier in April, Adobe updated its free Adobe Reader product to version 10.1.3 and 9.5.1. While fixing multiple vulnerabilities, the major change to the newly updated 9.5.1 version is the removal of a bundled Flash Player library file. This library file has been the source of many vulnerabilities in Adobe Reader as the vulnerability patch cycle for Acrobat Reader and Flash are different. This can be seen with version 10.1.3 which actually incorporated three previous Flash Player security updates that had been pushed out over the past three months.
Adobe does plan to remove the bundled Flash Player from the Adobe Reader 10.x in the near future, but currently the security sandbox built into the 10.x versions does provide a better level or protection than the previous versions (9.5.1 and below) that did not include the sandbox.
These changes will not affect most users as the PDF files that they use daily do not contain any Flash interactive content. For those that do use those type of PDFs, the 9.5.1 version of Reader will utilize the standalone Flash Player plug-in (usually used for Firefox, Safari or Opera).
You can find more details on the specifics on this Adobe Blog Post.
I highly recommend all users update their Adobe Acrobat Reader by running the Adobe Update utility under the Help menu, or going directly to Adobe's website to download and install the latest version (10.1.3)
While the above information is primarily targeted at Windows users, Adobe did update the mac versions of Adobe reader as well. As this CNET article points out, even the smallest patch to a widely distributed program can protect your system from future infections since these updates resolve problems that could cause the application to crash and potentially allow an attacker to take control of the affected system.
Source: Computerworld
Adobe does plan to remove the bundled Flash Player from the Adobe Reader 10.x in the near future, but currently the security sandbox built into the 10.x versions does provide a better level or protection than the previous versions (9.5.1 and below) that did not include the sandbox.
These changes will not affect most users as the PDF files that they use daily do not contain any Flash interactive content. For those that do use those type of PDFs, the 9.5.1 version of Reader will utilize the standalone Flash Player plug-in (usually used for Firefox, Safari or Opera).
You can find more details on the specifics on this Adobe Blog Post.
I highly recommend all users update their Adobe Acrobat Reader by running the Adobe Update utility under the Help menu, or going directly to Adobe's website to download and install the latest version (10.1.3)
While the above information is primarily targeted at Windows users, Adobe did update the mac versions of Adobe reader as well. As this CNET article points out, even the smallest patch to a widely distributed program can protect your system from future infections since these updates resolve problems that could cause the application to crash and potentially allow an attacker to take control of the affected system.
Source: Computerworld
Wednesday, April 18, 2012
Seamless Spellcheck for IE - Speckie
While I'm a die-hard Firefox user, there are times that I must use Internet Explorer to interact with a website. Many of those times are when I'm needing to type more than just my name, address and phone number. This is when a real-time seamless spellchecker would come in handy. While I believe Microsoft is working on add this capability to the future release of IE 10, there is an add-on called Speckie that works nearly everywhere! With compatibility for IE6, IE7, IE8 & IE9, it works on Windows XP, Vista & Windows 7 - including 64 bit versions of the browser!
I highly recommend you download & install Speckie and enjoy.
I highly recommend you download & install Speckie and enjoy.
Tuesday, April 17, 2012
Mac Malware - Flashback Roundup
In the ongoing battle against the Flashback malware, Apple released a third set of updates to Java last week. This new release includes a tool that will detect and remove the Flashback malware from infected Mac OS X 10.6 and 10.7 systems. But Apple has decided that it may even be able to protect it's users from Java malware with a more proactive approach. The new Java update will monitor itself and determine if it has been used during the past 35 days. If Java has not been used, it will automatically disable the Java settings and Users can re-enable the automatic execution of Java applets via the Java Preferences application (Applications ➤ Utilities ➤ Java Preferences). This means that any malware attack targeting Java would not be able to automatically infect users (aka drive-by infections) that rarely use Java. CNET has a great article on how this works in the real world.
Now Apple did release a stand alone detection and removal tool for OS X 10.7 Lion systems that may not have had Java installed. I'm fairly certain those systems would not have been effected, but I am happy Apple released this. You can download the standalone tool here.
While I applaud Apple for this new security minded approach, it still does not protect users of older Mac OS X versions (10.5 and below). Even users of OS X 10.6 Snow Leopard will not benefit from the automatic disable feature as it only works in 10.7 Lion. I still recommend disabling & removing Java if possible in for OS X 10.6 or below to prevent any further infections.
For Mac OS X users of any version (getting Apple updates or not), I highly recommend that you download and run one of the stand alone detection and removal tools made available from the security vendors:
F-secure Flashback Removal Tool
Kasperky (Updated Monday as the original had a flaw) - Flashfake/Flashback Removal Tool
Symantec - Norton Flashback Removal Tool
And all of these vendors have Mac Antivirus/Security software that should be evaluated and installed by businesses and individuals alike. The days of the Mac's security by obscurity has come to an end, and there are some major lessons for IT to be learned by the entire Flashback affair.
Now Apple did release a stand alone detection and removal tool for OS X 10.7 Lion systems that may not have had Java installed. I'm fairly certain those systems would not have been effected, but I am happy Apple released this. You can download the standalone tool here.
While I applaud Apple for this new security minded approach, it still does not protect users of older Mac OS X versions (10.5 and below). Even users of OS X 10.6 Snow Leopard will not benefit from the automatic disable feature as it only works in 10.7 Lion. I still recommend disabling & removing Java if possible in for OS X 10.6 or below to prevent any further infections.
For Mac OS X users of any version (getting Apple updates or not), I highly recommend that you download and run one of the stand alone detection and removal tools made available from the security vendors:
F-secure Flashback Removal Tool
Kasperky (Updated Monday as the original had a flaw) - Flashfake/Flashback Removal Tool
Symantec - Norton Flashback Removal Tool
And all of these vendors have Mac Antivirus/Security software that should be evaluated and installed by businesses and individuals alike. The days of the Mac's security by obscurity has come to an end, and there are some major lessons for IT to be learned by the entire Flashback affair.
Monday, April 16, 2012
Andorid Apps: TogglePanel & Wigetsoid
There are some phone management tasks that I do so frequently it becomes a hassle to go 3 or 4 screens deep just to do something as simple as dim the screen. My personal phone is an iPhone 4, and there's a nice app called SBSettings that allows me to do this since my phone is jailbroken. On the Android side there are multiple apps available to accomplish this, the two that I would recommend are: Widgetsoid and TogglePanel.
Both of these apps make it easy to get to settings such as wifi, Bluetooth, GPS, and brightness from the notifications drop down.
You can get TogglePanel from the Google Play store ($1). Be aware this requires Android 4.0 ICS.
You can get Widgetsoid from the Google Play store (free). This should work on most other Android versions 2.1 and up.
Both of these apps make it easy to get to settings such as wifi, Bluetooth, GPS, and brightness from the notifications drop down.
You can get TogglePanel from the Google Play store ($1). Be aware this requires Android 4.0 ICS.
You can get Widgetsoid from the Google Play store (free). This should work on most other Android versions 2.1 and up.
Friday, April 13, 2012
AT&T (and Apple) will Unlock your iPhone
Starting this past Sunday, AT&T started unlocking customer iPhones upon request. You have to have fulfilled your contract commitment and be in up to date with your bill. There may be other restrictions, but when you contact AT&T they will check your eligibility.
Why would you want to unlock your phone? Well, being able to use a different carrier is usually the main reason. You can use T-Mobile USA but you will mainly only get EDGE data rates. The other big reason would become apparent to any international traveler. An unlocked phone would all you to pick up a pre-paid SIM card in your country of choice and not have to pay the expensive international roaming call and data rates AT&T charges.
iPhone enthusiast website Redmond Pie has a great How To Unlock page providing step by step instructions.
Why would you want to unlock your phone? Well, being able to use a different carrier is usually the main reason. You can use T-Mobile USA but you will mainly only get EDGE data rates. The other big reason would become apparent to any international traveler. An unlocked phone would all you to pick up a pre-paid SIM card in your country of choice and not have to pay the expensive international roaming call and data rates AT&T charges.
iPhone enthusiast website Redmond Pie has a great How To Unlock page providing step by step instructions.
Wednesday, April 11, 2012
Mac Flashback Botnet Update - also Easy Detection & Cleanup Tools
There's been a lot of news about this since I last posted, so here are all the updates:
PCWorld has a great FAQ that goes over many details of the Flashback trojan/botnet and sets the record straight on a number of the details. The biggest fact that people out there are getting wrong is that this was never an Adobe Flash vulnerability. It has always been a Java based attack that is masquerading as an Adobe Flash update/installer (which is how it got it's name - Flashback). This is also the same type of Java based trojan that targets Windows computers too.
Apple has been slow to pull the trigger on Java updates for YEARS and has been chastised by the security community for it for a long time. The update that Apple released last week moved Java from Version 6 update 29 to Version 6 update 31. There was even a re-release of the update for Lion. But what happened to update 30 you ask? Good question. Apple took nearly two months to release update 31 from when Oracle had updated it. But when did update 30 come out? A quick look at the Wikipedia Java article says December 13, 2011. That's right, Apple took nearly 5 months to come out with an update for a Java vulnerability that was being actively exploited in update 29 that had could have been mostly fixed before January 1, 2012. There was an vulnerability in update 30 that started being utilized in mid-March to infect users - one month after Oracle has patched it with Java 6 update 31.
Now that Apple has seen Kaspersky independently confirm 600,000+ infected users, it is trying to do the right thing, unfortunately it is not going about it the right way. Apple has never really worked with the security community before to protect their users. I think it is time for Apple to have a big non-secretive pow-wow with all the global security companies and actually follow Microsoft's lead in collaborating to keep their users safe.
Kaspersky has created a very easy to use website called flashbackcheck.com to let you see if your Mac is infected. If you'd rather download a utility that will actually scan your computer to find out if it is infected, you can get that here.
And should you find that you are infected, you could manually clean your computer with the directions that F-Secure posted previously here and here , or you could download and run the free cleanup tool from Kaspersky.
And finally, as I stated in a previous post, if you are not utilizing Java - disable and uninstall it and then install a reputable antivirus/antimalware software package to help keep you safe. More steps on how to secure your Mac from Kaspersky are available here.
UPDATE: Late Tuesday, Apple announced that they are currently developing a tool to detect and remove the Flashback malware but they did not state when this tool would be available.
PCWorld has a great FAQ that goes over many details of the Flashback trojan/botnet and sets the record straight on a number of the details. The biggest fact that people out there are getting wrong is that this was never an Adobe Flash vulnerability. It has always been a Java based attack that is masquerading as an Adobe Flash update/installer (which is how it got it's name - Flashback). This is also the same type of Java based trojan that targets Windows computers too.
Apple has been slow to pull the trigger on Java updates for YEARS and has been chastised by the security community for it for a long time. The update that Apple released last week moved Java from Version 6 update 29 to Version 6 update 31. There was even a re-release of the update for Lion. But what happened to update 30 you ask? Good question. Apple took nearly two months to release update 31 from when Oracle had updated it. But when did update 30 come out? A quick look at the Wikipedia Java article says December 13, 2011. That's right, Apple took nearly 5 months to come out with an update for a Java vulnerability that was being actively exploited in update 29 that had could have been mostly fixed before January 1, 2012. There was an vulnerability in update 30 that started being utilized in mid-March to infect users - one month after Oracle has patched it with Java 6 update 31.
Now that Apple has seen Kaspersky independently confirm 600,000+ infected users, it is trying to do the right thing, unfortunately it is not going about it the right way. Apple has never really worked with the security community before to protect their users. I think it is time for Apple to have a big non-secretive pow-wow with all the global security companies and actually follow Microsoft's lead in collaborating to keep their users safe.
Kaspersky has created a very easy to use website called flashbackcheck.com to let you see if your Mac is infected. If you'd rather download a utility that will actually scan your computer to find out if it is infected, you can get that here.
And should you find that you are infected, you could manually clean your computer with the directions that F-Secure posted previously here and here , or you could download and run the free cleanup tool from Kaspersky.
And finally, as I stated in a previous post, if you are not utilizing Java - disable and uninstall it and then install a reputable antivirus/antimalware software package to help keep you safe. More steps on how to secure your Mac from Kaspersky are available here.
UPDATE: Late Tuesday, Apple announced that they are currently developing a tool to detect and remove the Flashback malware but they did not state when this tool would be available.
Monday, April 09, 2012
The iPad & Polarized Sunlgasses don't get along.
I ran across someone in public a few days ago trying to use their iPad while enjoying lunch outside on a bright sunny day. The person happened to be wearing sunglasses and was reading email in landscape mode (turned on its side). After finishing up email, he turned the iPad back to the "normal" orientation - portrait - and had a puzzled look on his face. He then proceeded to turn it in every direction and ended up using it in landscape mode again. While I was only observing, I was wondering what the problem might be. Well today, I found this gem in my news feed.
Apparently Apple has the iPad display polarized vertically and can cause problems when viewed through polarized glasses in it's normal portrait orientation. See the video below:
Apparently Apple has the iPad display polarized vertically and can cause problems when viewed through polarized glasses in it's normal portrait orientation. See the video below:
Thursday, April 05, 2012
The Mac Java Problem
Shortly after I posted about the Flashback Java malware targeting Mac OS X systems on Monday, Apple pushed out updates to Java for versions 10.6 and 10.7 of the operating system. While this brings those two versions, Snow Leopard & Lion respectively, up-to-date older versions of OS X (10.5 and earlier) did not receive any updates which leave them extremely vulnerable.
F-Secure has posted some information about how rapidly this malware is spreading. It has already reached 600,000 infected systems and is climbing, with over half of these infections in the United States. You should check to see if you are infected. Details are located here on how to do this.
As I posted on Monday, F-secure also found a Flashback variant that was exploiting a vulnerability that had not been patched yet, the newest update from Apple will most likely prevent users from getting infected. But Apple is notorious for not pushing out Java updates as quickly as Oracle releases them. This means that it's just a matter of time before users are not protected against attacks.
What will protect users from getting infected? I recommend the following course of action:
1) - Evaluate what programs, websites, web apps you are using and determine if any require Java. You are most likely going to come up with very few if any require Java. This will lead you to step two.
2) - If none of your websites or web apps utilize Java, then disable it immediately inside your browser of choice. Maclife has a great article that has all the steps on doing this in Safari, Firefox and Chrome. Actually I recommend doing this EVEN IF you have websites that need Java. You can always turn it back on temporarily, exit your browser and open it back up to use the website or web app. It is IMPERATIVE that you disable Java again immediately after you are finished your task.
3) - If you do not have anything that uses Java, then I recommend UNINSTALLING IT COMPLETELY! CNET's MacFixit Blog has information on how to perform the uninstall. And I highly suggest ALL Mac OS X users uninstall Java from their computers.
4) - Do you have any security software installed? Most likely you do not. There has been a sense for a long time that Macs are not vulnerable to malware. Over the past few years this has changed, but this year is when we must draw the line and begin protecting all Macs. As I mentioned previously, F-Secure has a great product that will protect you from muti-vector infections. There is also an offering from Intego that is very reputable. And Sophos has a free product for home use that can provide protection.
5) - Please be aware, that there is a good chance that every time Apple releases a new update, you may have to disable/uninstall Java again.
At this point, you should be protected, but we all have to be ever vigilant as the Mac OS X install base is target.
F-Secure has posted some information about how rapidly this malware is spreading. It has already reached 600,000 infected systems and is climbing, with over half of these infections in the United States. You should check to see if you are infected. Details are located here on how to do this.
As I posted on Monday, F-secure also found a Flashback variant that was exploiting a vulnerability that had not been patched yet, the newest update from Apple will most likely prevent users from getting infected. But Apple is notorious for not pushing out Java updates as quickly as Oracle releases them. This means that it's just a matter of time before users are not protected against attacks.
What will protect users from getting infected? I recommend the following course of action:
1) - Evaluate what programs, websites, web apps you are using and determine if any require Java. You are most likely going to come up with very few if any require Java. This will lead you to step two.
2) - If none of your websites or web apps utilize Java, then disable it immediately inside your browser of choice. Maclife has a great article that has all the steps on doing this in Safari, Firefox and Chrome. Actually I recommend doing this EVEN IF you have websites that need Java. You can always turn it back on temporarily, exit your browser and open it back up to use the website or web app. It is IMPERATIVE that you disable Java again immediately after you are finished your task.
3) - If you do not have anything that uses Java, then I recommend UNINSTALLING IT COMPLETELY! CNET's MacFixit Blog has information on how to perform the uninstall. And I highly suggest ALL Mac OS X users uninstall Java from their computers.
4) - Do you have any security software installed? Most likely you do not. There has been a sense for a long time that Macs are not vulnerable to malware. Over the past few years this has changed, but this year is when we must draw the line and begin protecting all Macs. As I mentioned previously, F-Secure has a great product that will protect you from muti-vector infections. There is also an offering from Intego that is very reputable. And Sophos has a free product for home use that can provide protection.
5) - Please be aware, that there is a good chance that every time Apple releases a new update, you may have to disable/uninstall Java again.
At this point, you should be protected, but we all have to be ever vigilant as the Mac OS X install base is target.
Monday, April 02, 2012
Mac Malware: 2012 is shaping up to be busy
So far this year it is becoming clear that Mac OS X users everywhere are going to need to ensure they are protected from the growing malware threats being developed.
The Flashback family of malware utilize Java vulnerabilities (patched and unpatched zero-day) and were named due to their original attempt to identify themselves as (fake) Flash Player updates. Most of the older Flashback variants are utilizing patched Java vulnerabilities. Users that have fully patched and updated systems would not be vulnerable to these.
F-Secure has a new article outlining a new variant that attacks the system through a new unpatched vulnerability in Java for Mac OSX. The only way to mitigate this threat is to disable Java completely as users must wait for Apple to release a patch (Oracle already released an update for this vulnerability across all other OSes earlier this year).
Then there are the new attacks (currently target Tibetan NGOs) that utilize vulnerabilities in MS Office for Mac 2004 and 2008. While Microsoft has already patched these, users must have all their updates installed in order to not find themselves a target in the future.
With all of this said, I would highly recommend to any Mac user, business or personal, that they purchase and install reputable security/anti-virus/anti-malware software, such as the offering from F-Secure.
The Flashback family of malware utilize Java vulnerabilities (patched and unpatched zero-day) and were named due to their original attempt to identify themselves as (fake) Flash Player updates. Most of the older Flashback variants are utilizing patched Java vulnerabilities. Users that have fully patched and updated systems would not be vulnerable to these.
F-Secure has a new article outlining a new variant that attacks the system through a new unpatched vulnerability in Java for Mac OSX. The only way to mitigate this threat is to disable Java completely as users must wait for Apple to release a patch (Oracle already released an update for this vulnerability across all other OSes earlier this year).
Then there are the new attacks (currently target Tibetan NGOs) that utilize vulnerabilities in MS Office for Mac 2004 and 2008. While Microsoft has already patched these, users must have all their updates installed in order to not find themselves a target in the future.
With all of this said, I would highly recommend to any Mac user, business or personal, that they purchase and install reputable security/anti-virus/anti-malware software, such as the offering from F-Secure.
Friday, March 30, 2012
While I used an Android phone (Droid 3) at my previous job, I toyed with a number of scheduling or location aware apps to change the settings on my phone automatically. Over the past month, there have been a few released that I would enjoy testing out. Since my personal phone is an iPhone 4, I'll just have to wait. But I'll share the information so that those of you out there may be able to enjoy the simplicity that automation can bring.
WiFi Timer for Android
If you have a regular or semi-regular schedule where you are in and out of wifi areas and would like to maximize your battery life, this app may be for you. From the screenshots, this appears to be quite simple to setup. You can find more information over at redmondpie.
Silent Time!
There are times daily and weekly that I set my phone to vibrate only. With this being a regular occurrence, scheduling it would save all the problems that arise if I actually forget to change the setting. This is where Silent Time! could save the day. Much like WiFi Timer above, it appears you can automate your regularly scheduled silent/vibrate times. You can find more information over at redmondpie.
Llama for Android
If you have more complex scheduling needs, especially ones that are location based, this app may be for you. This lets you setup custom profiles to be triggered based on Location (GPS), WiFi connection, Date, Time and possibly other triggers. You can find more information over at redmondpie.
WiFi Timer for Android
If you have a regular or semi-regular schedule where you are in and out of wifi areas and would like to maximize your battery life, this app may be for you. From the screenshots, this appears to be quite simple to setup. You can find more information over at redmondpie.
Silent Time!
There are times daily and weekly that I set my phone to vibrate only. With this being a regular occurrence, scheduling it would save all the problems that arise if I actually forget to change the setting. This is where Silent Time! could save the day. Much like WiFi Timer above, it appears you can automate your regularly scheduled silent/vibrate times. You can find more information over at redmondpie.
Llama for Android
If you have more complex scheduling needs, especially ones that are location based, this app may be for you. This lets you setup custom profiles to be triggered based on Location (GPS), WiFi connection, Date, Time and possibly other triggers. You can find more information over at redmondpie.
Subscribe to:
Posts (Atom)